51 Which of the Following Best Describes Data Accessibility
Which of the following best describes an AWS Region. Which data access technology should you recommend.

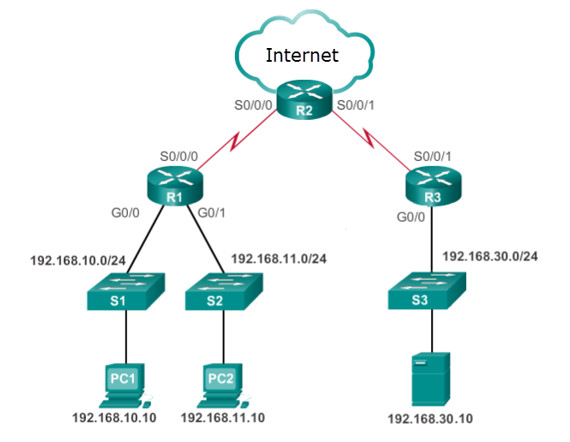
Ccna 3 V7 Modules 3 5 Network Security Exam Answers
2 It is followed by formation of a hypothesis which is the expected outcome of the interaction of the variable factors.
. Which of the following would BEST describes the solution the analyst should pursue. Which of the following best describes information security. Which of the following BEST protects against data theft in this instance.
The purpose of social engineering is to obtain access data like user IDs and passwords. The definition of data is knowledge used appropriately to manage and solve. The next step is collection of data or set of.
Two zones containing compute resources that are designed to automatically maintain synchronized copies of each others. Which of the following BEST describes what would occur if a packet. A Processed and analyzed in a formal intelligent way.
Which of the following best describes Availability Zones. B A collection of data. The Media Access Control MAC sublayer and the Logical Link Control LLC sublayer.
Start studying Test 51-100 First Part. Datamurders Next use the function str to examine the structure of the murders object. A - This pattern is used to get a way to access the elements of a collection object in sequential manner without any need.
Data are the synthesis of information derived from several sources to produce a single concept or idea. A A distinct location within a geographic area designed to provide high availability to a specific geography. Which of the following terms best describes the time it takes for a data packet to move from source to destination.
The gap between people with effective access to digital and information technology and those with very limited or no access at all II. Implement an IDS rule that contains the IP. 67You need to recommend a data access technology to the contractor to retrieve data from the new data source.
We can see that this object is a data frame with 51 rows and five columns. This preview shows page 10 - 12 out of 16 pagespreview shows page 10 - 12 out of 16 pages. Which two statements accurately describe characteristics of IPsec.
A security analyst needs to find real-time data on the latest malware and IoCs. The primary function of the American Health Information Management Association is ____. Question 155 Which statement about encryption is True about data in use.
To ensure that acurate and complete medical records are written for every hospital patient. The data link layer of the OSI model is divided into two sublayers. Implement an IPS rule that contains content for the malware variant and patch the routers to protect against the vulnerability.
Data are _____ whereas information is _____. Following BEST describes this situation. Choose two IPsec works at the transport layer and protects data at the network layer.
The mechanisms for safeguarding information and information systems The right of individuals to limit access to information. Learn vocabulary terms and more with flashcards games and other study tools. DSL is an always-on high bandwidth connection that runs over telephone lines.
The imbalance both in physical. Raw facts and figures collected by the organization b Raw. Data should always be kept encrypted since modern CPUs are fully capable of operating directly on.
Q 17 - Which of the following describes the Iterator pattern correctly. Cable uses the same coaxial cable that carries television signals into the home.
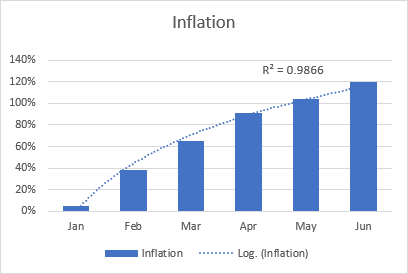
Excel Trendline Types Equations And Formulas

Ccna 3 V7 Modules 3 5 Network Security Exam Answers
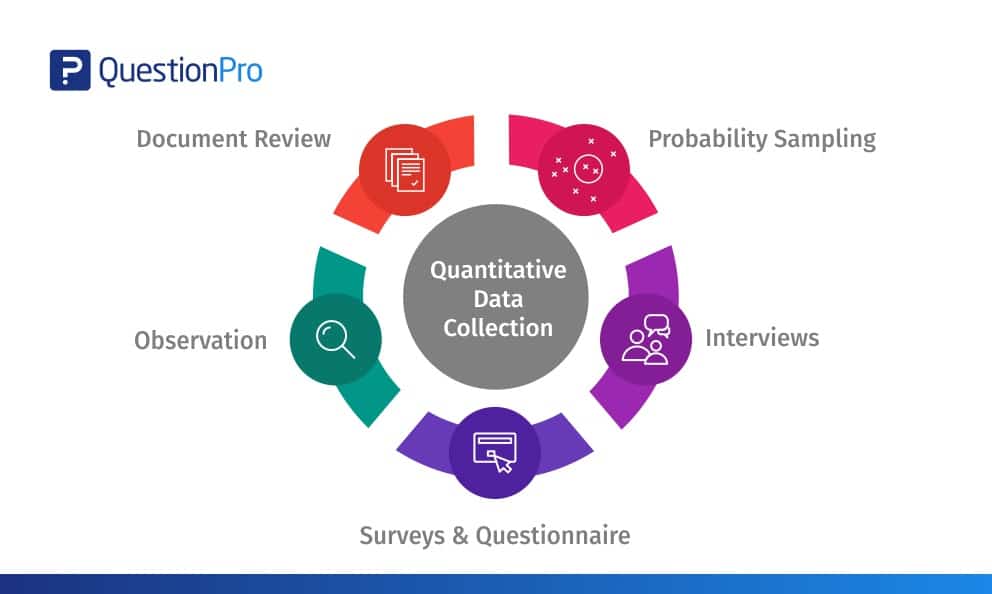
Quantitative Data Collection Best 5 Methods Questionpro

Restaurant And Catering Management Software Document Management System Access Database Database Management System
No comments for "51 Which of the Following Best Describes Data Accessibility"
Post a Comment